You can use an Active Directory Federation Services (ADFS) server as the claims
provider for Security
Center, and allow users outside
your company to log on to your system by establishing a trust chain from third-party's ADFS
servers to your company's Security
Center main
server.
Before you begin
It is assumed that you are familiar with the concepts of
claims-based authentication and that your
company's
ADFS server is operational. For general
information on ADFS installation and configuration, please refer to the documentation provided
by Microsoft.
What you should know
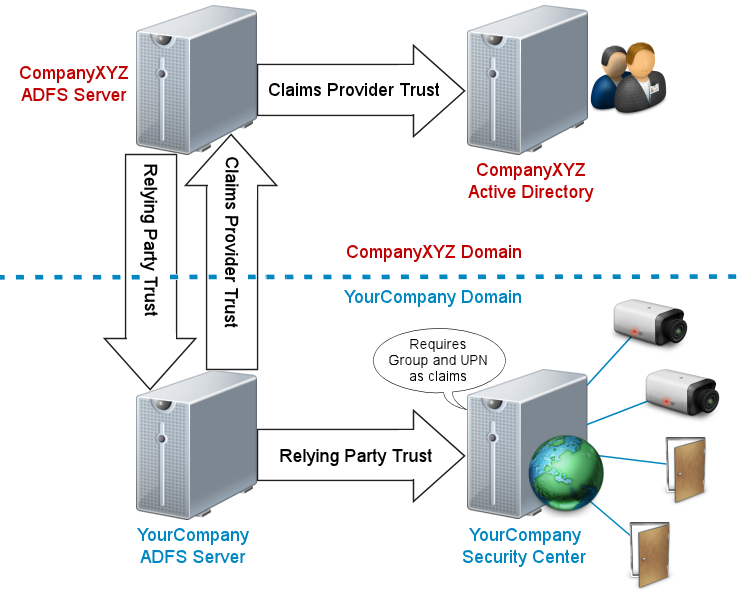
For illustration purposes, let's assume that you want to allow external users from
Company XYZ to access your company's Security
Center
system. Company XYZ has its own ADFS server that relies on its own Active Directory as claims provider. Company XYZ's servers are not on the same domain as your
company's servers. Your company's ADFS server relies on Company XYZ's ADFS server as claims
provider, and in turn, acts as claims provider to your company's Security
Center system. Therefore, a chain of trusts must be
established from the Company XYZ's Active Directory to the main server of your company's
Security
Center system. NOTE: Security
Center requires specific attributes as
claims:
Group and
UPN (User Principal
Name).
To deploy claims-based authentication through ADFS:
-
Configure the trust chain outside your company's domain.
Make sure that the following tasks are performed by the Company XYZ's IT
personnel.
-
Add a claims provider trust to Company XYZ's ADFS server for Company XYZ's Active
Directory.
-
Add a relying party trust to Company XYZ's ADFS server for your company's ADFS
server.
-
Configure your local ADFS server as the claims provider for your Security
Center system.
-
On your company's ADFS server, open the AD FS Management snap-in.
-
Add a claims provider
trust to your ADFS for the third-party ADFS server.
-
Configure the claim rules
for the third-party claims provider.
-
Add a relying party trust to your
ADFS server for Security
Center.
-
Configure the claim rules for
Security
Center, the relying party
you just added.
-
Configure your Security
Center system to
receive claims from your local ADFS server.
-
Connect to your Security
Center system with
Config
Tool.
-
Create a user group for each ADFS
group you accept as Security
Center user
groups.
-
Create the Active Directory Federation
Services role.
All users authenticated through ADFS must log on using fully qualified usernames,
meaning that they must add their domain name to their usernames, such as in
Username@CompanyXYZ.com.IMPORTANT: There is currently a
known issue regarding the use of a local Active Directory and ADFS. When you have external
users authenticated through ADFS in your system, all users imported from your local Active
Directory must also use fully qualified user names, even though they belong to the same
domain as your Security
Center
system.

