For an ADFS server to act as the claims provider for your Security
Center system, you must add your Security
Center system to the relying party trusts of the ADFS
server.
Before you begin
The
AD FS Management snap-in window must be open on your ADFS server. If
Directory failover is configured on
your system, have with you the hostname of each of your Directory servers.
What you should know
This task is part of the deployment process for claims-based
authentication using ADFS based on a sample scenario.
The sample screen captures are taken from Windows Server
2016. If you are using a different version, your screens might look different.NOTE: If you are not enabling
passive authentication, click
Next instead of executing the steps that are marked "(PA
only)".
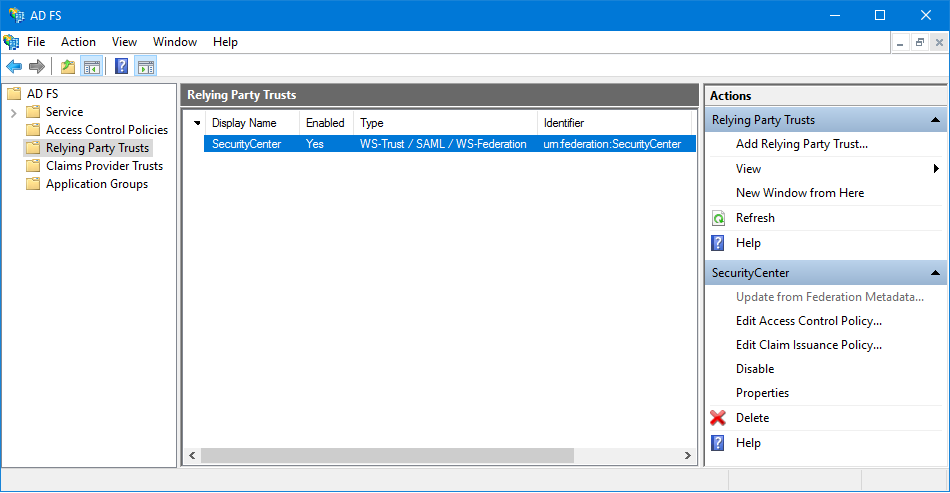
To add a relying party trust to your ADFS server for Security
Center:
-
In the AD FS window, click .
The Add Relying Party Trust Wizard window
opens
-
On the Welcome page, click .
You can leave Claims aware selected.
-
On the Specify Display Name page, enter in the Display
name field, a name that represents your company's Security
Center system, and click
Next.
For example, YourCompany Security
Center.
-
(Optional) On the Configure Certificate page, specify a token
encryption certificate and click Next.
-
(PA only) On the Configure URL page, select Enable
support for the WS-Federation Passive protocol and enter the URL of your
Security
Center
main server, and then click Next.
For example:
https://MainServer.YourCompany.com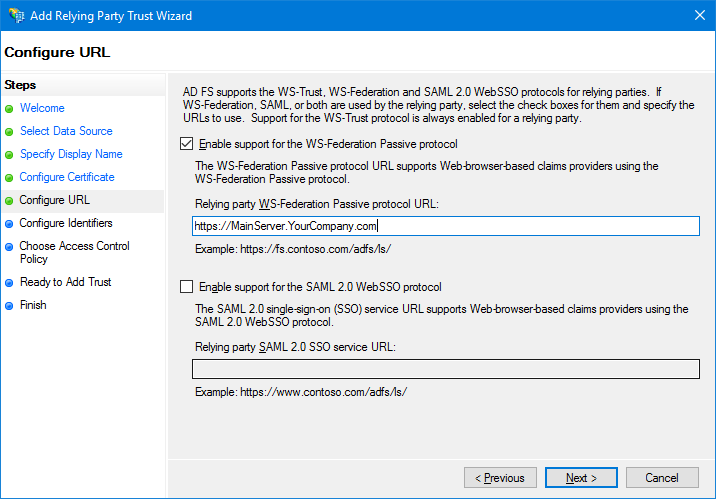
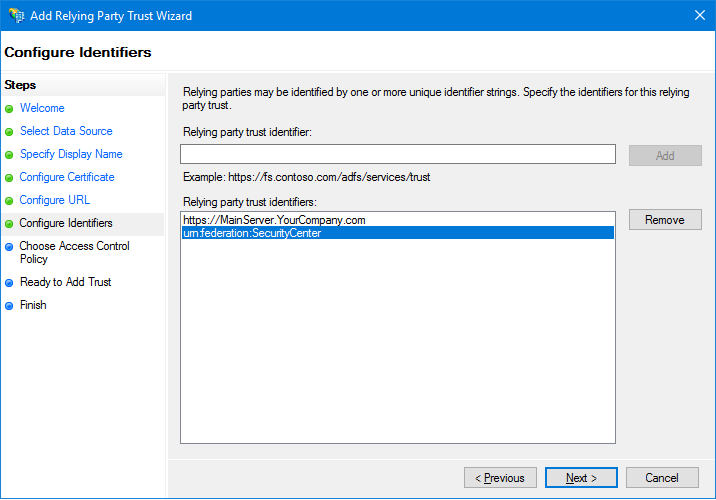
-
(PA only) On the Configure Identifiers page, enter in the
Relying party trust identifier field, a string that identifies
your Security
Center main server, and click
Add.
IMPORTANT: An example would be to use the URL of your main server:
https://MainServer.YourCompany.com. Write this value down. You
need to enter this identifier in a subsequent step, when you
configure your ADFS role on the
Security
Center server.
BEST PRACTICE: We recommend using the default value configured for the ADFS role,
urn:federation:SecurityCenter, so you have one less thing to
remember.
-
(PA only) In the Relying party trust identifiers list, select
the row that corresponds to your main server URL and click .
-
In the Choose Access Control Policy page, select Permit
everyone and click Next.
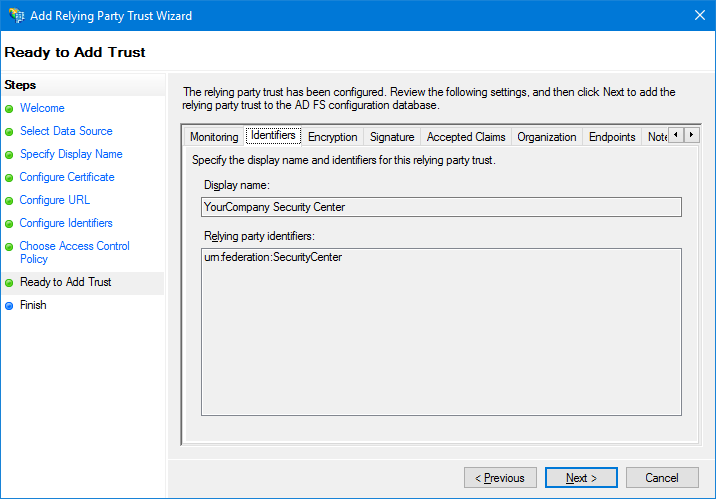
-
In the Ready to Add Trust page, click
Identifiers, and verify the identifiers you entered.
-
Click Next, leave Configure claims issuance policy
for this application selected, and click Close.
The Security
Center main server is added
to the relying party trusts of your ADFS server.
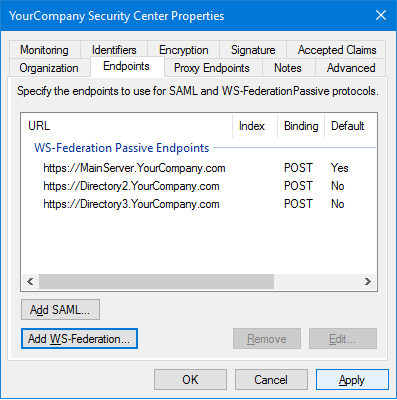
-
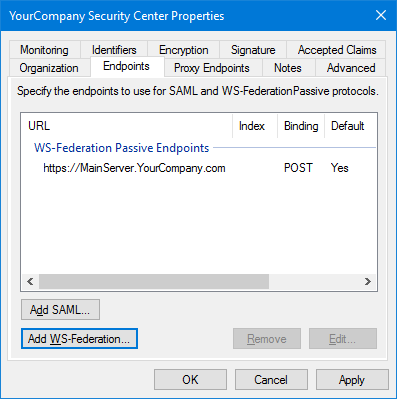
If Directory failover is configured on your system, you must add the URL of each
Directory server as endpoints to the Security
Center relying party trust of your ADFS server.
NOTE: The ADFS role runs on the same server as the Directory role. When the Directory role
fails over to the next server in line, the ADFS role also fails over to the same server.
For this reason, the ADFS server must know the URL of every Directory server you have in
your system. For the server URL, enter https:// followed by the
fully qualified hostname.
-
In the AD FS window, select the Security
Center relying party trust, and click .
-
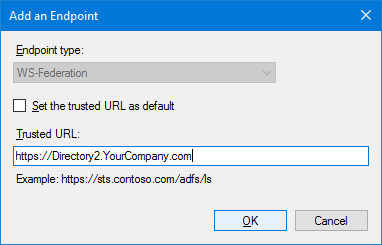
Click Add WS-Federation, enter the URL of a Directory
server, and click OK.
-
Repeat the previous step for all Directory servers on your system.
-
Click .