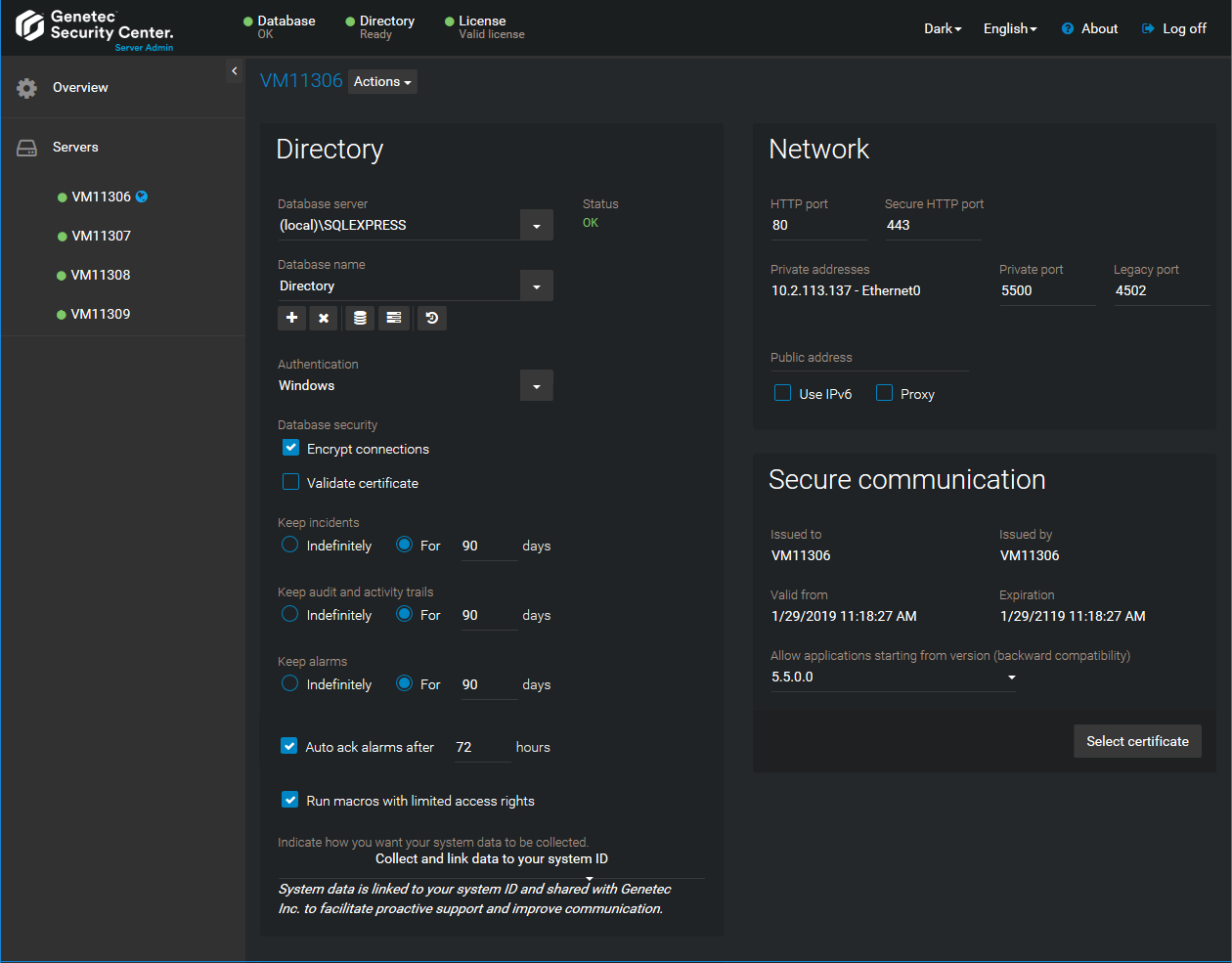
The Server Admin - Main server page lets you configure your Directory database and the settings pertaining to your main server.
Actions
Click the Actions drop-down list beside the server name to see what actions can be applied to the main server.The available actions are:
- Directory:
- Start/Stop:Start or stop the Directory.
- Restart:Restart the Directory.
- Deactivate:
Directory
The Directory section shows the status and settings of the Directory database. The Directory database contains all system and entity configurations, the incident reports, and the alarm history.NOTE: If you accessed
Server
Admin from Config
Tool instead of through a web browser, you do
not see the database commands (upgrading or restoring the database) because you are still
connected to the Directory. You cannot modify the Directory database while you are still
connected to it.
- Database server:
 Name of the SQL Server service. The value
Name of the SQL Server service. The value(local)\SQLEXPRESScorresponds to Microsoft SQL Server 2014 Express Edition installed by default with Security Center Server. - Database name:
 Name of the database instance (default =
Name of the database instance (default =Directory). - Actions:
 Maintenance functions you can perform on the Directory database:
Maintenance functions you can perform on the Directory database:- Database properties (
 ):
):  Opens a dialog box showing the database information, and the automatic Backup and Email notification settings.
Opens a dialog box showing the database information, and the automatic Backup and Email notification settings. - Show progress (
 ):
):  Opens a dialog box showing the past and current actions being performed on the database.
Opens a dialog box showing the past and current actions being performed on the database.
- Authentication:
 Specifies which SQL Server authentication is to be used:
Specifies which SQL Server authentication is to be used:- Windows:
 (Default) Use Windows authentication when the role server and the database server are on the same domain.
(Default) Use Windows authentication when the role server and the database server are on the same domain. - SQL Server:
 Use SQL Server authentication when the role server and the database server are not on the same domain. Mandatory for Azure SQL Database. You must specify a username and password in this case.
Use SQL Server authentication when the role server and the database server are not on the same domain. Mandatory for Azure SQL Database. You must specify a username and password in this case.
- Database security:
 Security options for communication between the role and its database server.
Security options for communication between the role and its database server.- Encrypt connections:
 (Default) Uses Transport Layer Security (TLS) protocol for all transactions between the role and the database server. This option prevents eavesdropping and requires no setup on your part.
(Default) Uses Transport Layer Security (TLS) protocol for all transactions between the role and the database server. This option prevents eavesdropping and requires no setup on your part. - Validate certificate:
 Authenticates the database server before opening a connection. This is the most secure communication method and prevents man-in-the-middle attacks. The Encrypt connections option must first be enabled.NOTE: You must deploy a valid identity certificate on the database server. A valid certificate is one that is signed by a certificate authority (CA) that is trusted by all servers hosting the role and that is not expired.
Authenticates the database server before opening a connection. This is the most secure communication method and prevents man-in-the-middle attacks. The Encrypt connections option must first be enabled.NOTE: You must deploy a valid identity certificate on the database server. A valid certificate is one that is signed by a certificate authority (CA) that is trusted by all servers hosting the role and that is not expired.
- Keep incidents:
 Specifies how long the incident reports are kept in the Directory database.
Specifies how long the incident reports are kept in the Directory database. - Keep audit and activity trails:
 Specifies how long the entity configuration history and the activity history are kept in the Directory database.
Specifies how long the entity configuration history and the activity history are kept in the Directory database. - Keep alarms:
 Specifies how long the alarm history is kept in the Directory database.
Specifies how long the alarm history is kept in the Directory database. - Auto ack alarms after:
 Lets the system automatically acknowledge all active alarms that do not get acknowledged before the specified time (default = 72 hours). When turned on, this option supersedes the Automatic acknowledgment option configured for each individual alarm. When the automatic acknowledgment of alarms is turned on at both the system and individual alarm level, it is the shortest delay that applies.
Lets the system automatically acknowledge all active alarms that do not get acknowledged before the specified time (default = 72 hours). When turned on, this option supersedes the Automatic acknowledgment option configured for each individual alarm. When the automatic acknowledgment of alarms is turned on at both the system and individual alarm level, it is the shortest delay that applies. - Run macros with limited access rights:
 Runs macros in a subprocess with limited access to the Directory host OS to protect the system from malicious macro execution.
Runs macros in a subprocess with limited access to the Directory host OS to protect the system from malicious macro execution. - Indicate how you want your system data to be collected:
 You can change your data collection preference selected at system installation. The options are:
You can change your data collection preference selected at system installation. The options are:- Do not collect data:No data is collected for product improvement.
- Collect data anonymously:System data are collected and shared with Genetec Inc., but all data that identify your company are first removed.
- Collect and link data to your system ID:System data are linked to your system ID and shared with Genetec Inc. to facilitate proactive support and improve communication.
Network
Use this section to configure the network card and the TPC listening port used by the Genetec™ Server service.- HTTP port:
 Port used by the Genetec™ Server service to listen to commands received from other Security Center servers on the public address.
Port used by the Genetec™ Server service to listen to commands received from other Security Center servers on the public address. - Secure HTTP port:
 Port used by Genetec™ Server service for secured HTTP connections.
Port used by Genetec™ Server service for secured HTTP connections. - Private address:
 List of private addresses corresponding to the network interface cards (NIC) installed on this server. Only select the ones that are used for the communication between Security Center applications.
List of private addresses corresponding to the network interface cards (NIC) installed on this server. Only select the ones that are used for the communication between Security Center applications. - Private port:
 Port used by the main server to listen to incoming connection requests, and by all servers for communication between themselves, on the private IP address. (default = 5500).NOTE: If you change this port on the main server, then all users must specify the new port number after the Directory name in the Logon dialog box, separated by a colon (:). This applies to all expansion servers. You must specify the new port number after the Security Center Directory name in Server Admin, in the Main server connection section.
Port used by the main server to listen to incoming connection requests, and by all servers for communication between themselves, on the private IP address. (default = 5500).NOTE: If you change this port on the main server, then all users must specify the new port number after the Directory name in the Logon dialog box, separated by a colon (:). This applies to all expansion servers. You must specify the new port number after the Security Center Directory name in Server Admin, in the Main server connection section. - Legacy port:
 Port used by the Genetec™ Server service to listen to commands received from servers running an older version of Security Center (default = 4502).
Port used by the Genetec™ Server service to listen to commands received from servers running an older version of Security Center (default = 4502). - Public address:
 Public address of the server.
Public address of the server.- Use IPv6:
 Use IPv6 for video streaming and communication between servers (only if your network supports it).
Use IPv6 for video streaming and communication between servers (only if your network supports it). - Proxy:
 Select this option if the server is used as the proxy server for a private network protected by a firewall.
Select this option if the server is used as the proxy server for a private network protected by a firewall.
Secure communication
Use this section to view the current identity certificate used by the server to communicate with other Security Center servers.- Issued to:
 Subject of the current certificate. A self-signed certificate created at software installation appears in the form GenetecServer-{MachineName}.
Subject of the current certificate. A self-signed certificate created at software installation appears in the form GenetecServer-{MachineName}. - Issued by:
 Name of the certificate authority that issued the certificate. The issuer and the subject are the same for self-signed certificates.
Name of the certificate authority that issued the certificate. The issuer and the subject are the same for self-signed certificates. - Valid from/Expiration:
 Validity period of the current certificate.
Validity period of the current certificate.
- Select certificate (button):
 Dialog box listing all certificates installed on this machine. You can use this dialog box to change the certificate used for this server.
Dialog box listing all certificates installed on this machine. You can use this dialog box to change the certificate used for this server.
- Allow application starting from version (backward compatibility):
 To increase system security, limit backward compatibility to your current version (5.8). Select an older version if you have expansion servers running older versions in your system.
To increase system security, limit backward compatibility to your current version (5.8). Select an older version if you have expansion servers running older versions in your system.
