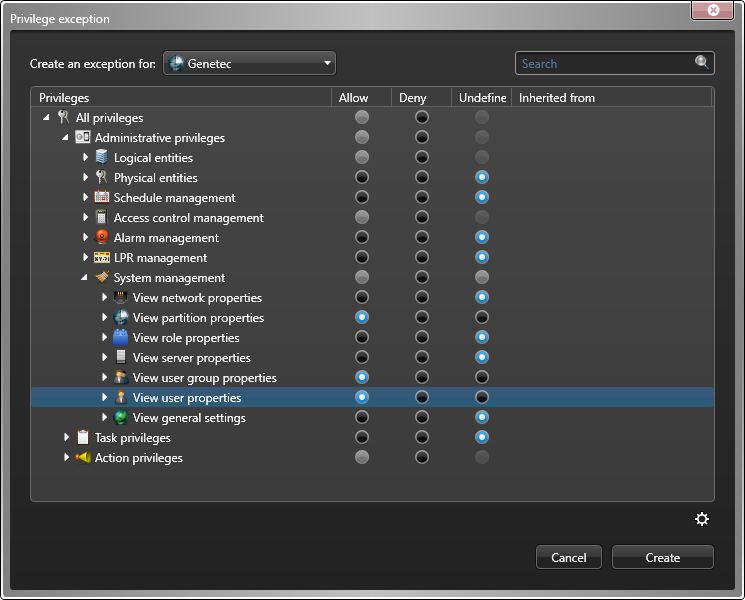
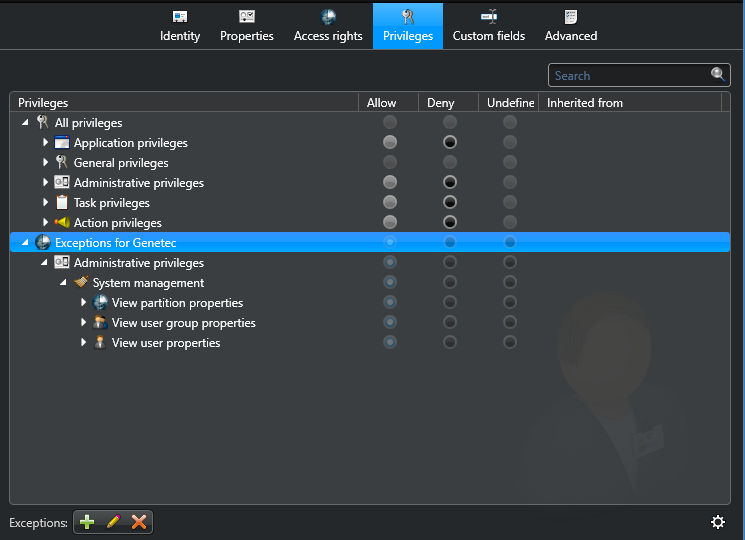
You must grant privileges to users for them to do anything in Security Center, including logging on, using Security Desk, and so on.
What you should know
BEST PRACTICE: Individual users should only have the
minimum required privileges. When assigning privileges, Security
Center offers templates, with predefined sets of
privileges, that can be applied to users or groups.
To help you better understand what your users can do, Security Center includes a Privilege troubleshooter. The Privilege troubleshooter is a tool that helps you investigate the allocation of user privileges in your Security Center system. Use the troubleshooter to verify access rights and help you fix issues.
To assign privileges to a user: