Directory authentication is a Security Center option that forces all client and server applications on a given machine to validate the identity certificate of the Directory before connecting to it. This measure prevents man-in-the-middle attacks.
When do I need Directory authentication?
The purpose of Directory authentication is to protect against man-in-the-middle attacks. If you do not have applications connecting to your system over the Internet (or any untrusted network), the potential for this sort of attacks is very low. In that case, you are probably safe not to enable this option.
What is an identity certificate?
An identity certificate, also known as a digital certificate or public key certificate, is a digitally signed document that allows a computer or an organization to exchange information securely over a public network. The certificate includes information about the owner's identity, the public key used to encrypt future messages sent to the owner, and the digital signature of the certificate authority (CA).
How it works
When installing the Server components of Security Center, a self-signed certificate named GenetecServer-{MachineName} is automatically created in the Local Computer Certificate Store. You can view the current certificate in Server Admin, in your server page, under the Secure communication section.
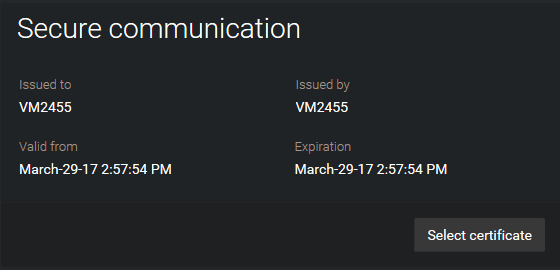
The self-signed certificates are used to identify the expansion servers to the main server, so the password used to connect to the main server does not need to be stored locally on the expansion servers.
Directory authentication is enabled at Security Center installation when you choose the recommended security settings, or by selecting Always validate the Directory certificate when you choose the custom security settings. For more information, see the Security Center Installation and Upgrade Guide.
If you choose to keep the self-signed certificate on the main server, then the first time a workstation is used to connect to the Directory, the user will be prompted to confirm that the Directory server can be trusted.
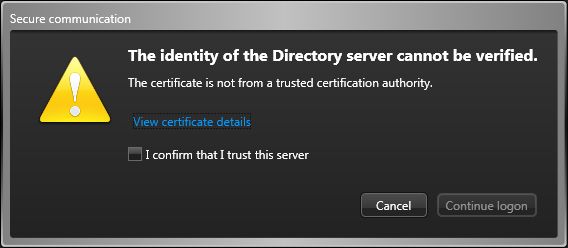
Once a user confirms that the main server can be trusted, the certificate is whitelisted, and the dialog box will not appear again.
The same confirmation is required on expansion servers. The first time you log on to the expansion server with Server Admin, you will see this message on the dashboard.

You must click on Main server connection, and then click Accept certificate in the dialog box that appears.
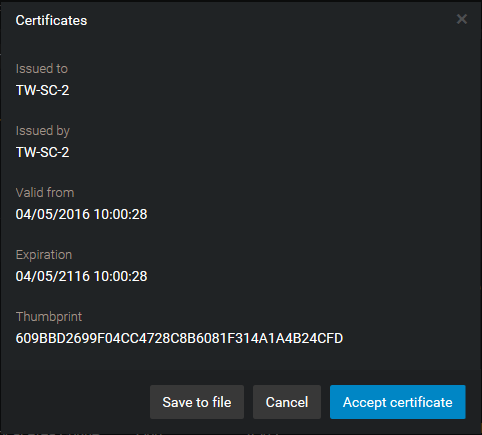
Once the main server is confirmed, you can change the password or the certificate on either the main server or the expansion server, and never have to confirm your trust again, as long as the two servers stay connected while you make the change.
Requirements
- DNS must be configured on the network. Servers and client workstations must be able to resolve the main server name.
- The main server name must be resolved by the DNS to the common name on the Directory certificate.
- Client workstations and expansion servers must be able to trust the certificate provided by main server. Otherwise, a user intervention is always required to accept the certificate the first time a machine is used to connect to the main server.
How do I change this setting after installation?
To change the Directory authentication setting after software installation, you must edit the GeneralSettings.gconfig file on each computer where you want it changed.
