To monitor and control Security
Desks
remotely, you must connect to one remote Security
Desk workstation (Simple mode), or
multiple remote Security
Desk monitors
(Wall mode).
What you should know
For information about the Remote task, see Remote monitoring.
To connect to remote Security
Desks:
-
From the home page, open the Remote task.
-
To connect to one remote Security
Desk, select a remote Security
Desk workstation from the drop-down list, or to connect to multiple remote Security
Desk monitors, proceed as follows:
-
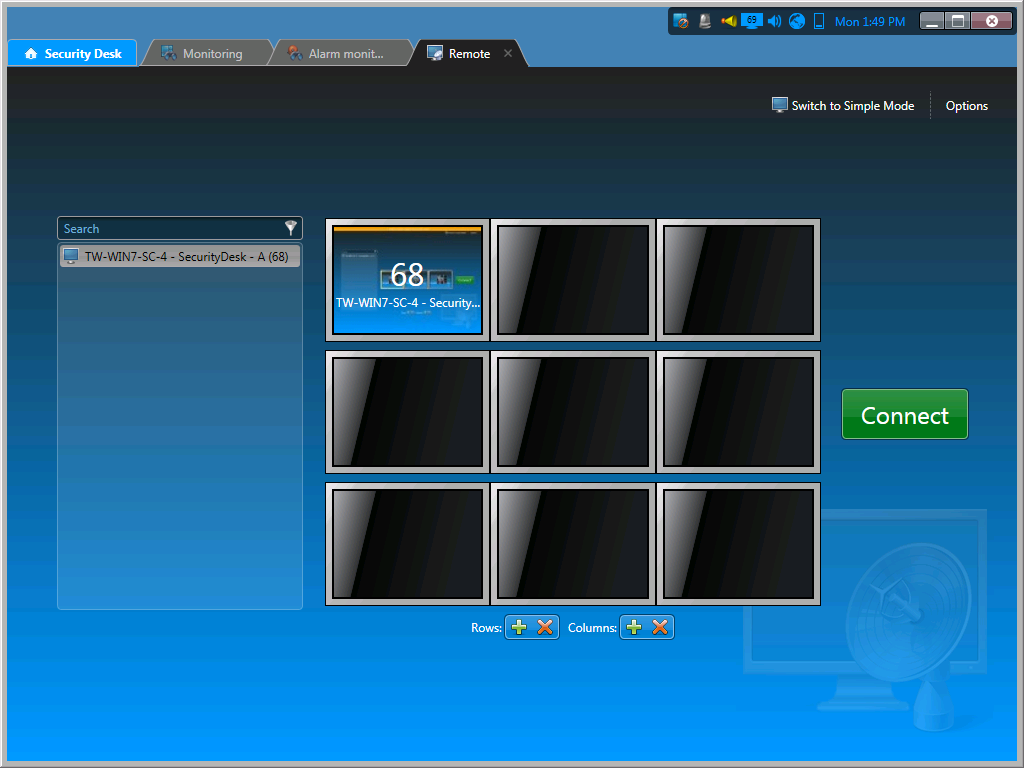
Click Switch to Wall mode.
-
To configure the layout of your wall, use the
 and
and  buttons in theRows and
Columns sections.
buttons in theRows and
Columns sections.
-
From the drop-down list, double-click the remote Security
Desk monitors you want
to connect to.
The monitors you select populate the empty tiles. To remove a
monitor from a tile, click

in the
tile.
-
(Optional) Click Options and
select one or both of the following:
Spy mode:

Allows you to connect to a remote Security
Desk undetected. In this mode, you
cannot perform any actions, you can only observe.
Low bandwidth:

Ensures that your bandwidth does not increase while
remotely monitoring a Security
Desk.This option is helpful because every command executed on the remote
Security
Desk is also executed on
your local Security
Desk, which
might increase your bandwidth.
-
Click Connect.
You are connected to the remote Security
Desk. If you are using Wall mode, the monitor that was placed in the first tile is displayed.
After you finish
When you are connected, you can view the tasks that were already opened on the remote
Security
Desk. However, you can only
use the Monitoring task and the Alarm monitoring task. For all other
tasks, the following message is displayed: This task cannot be remotely
controlled.NOTE: On the remote
Security
Desk, the number of users that are
remotely controlling it are indicated on the
Remote monitoring icon in the notification tray
(

), unless those
users are in Spy mode. Click the
Remote monitoring icon to view which users are
remotely controlling your
Security
Desk, and which system they are on. If you have the user privilege, you can kick those
users out of your
Security
Desk.

