Security Center Synergis™ is the IP access control system (ACS) that heightens your organization’s physical security and increases your readiness to respond to threats. Supporting an ever-growing portfolio of third-party door control hardware and electronic locks, it allows you to leverage your existing investment in network and security equipment.
Synergis™ was designed with an open and distributed architecture. You can build your system with new IP readers or use what you already have. Integrate your access control system with other third-party systems, like intrusion or building management, and distribute Synergis™ server components on many different network machines to optimize bandwidth and workload.
Synergis™ Enterprise supports an unrestricted number of doors, controllers and client workstations. You can grow your system one door at a time or scale your system across multiple buildings using the Federation™ feature.
How Synergis™ works
Synergis™ architecture is based on the server role known as the Access Manager, which controls the physical door controllers.
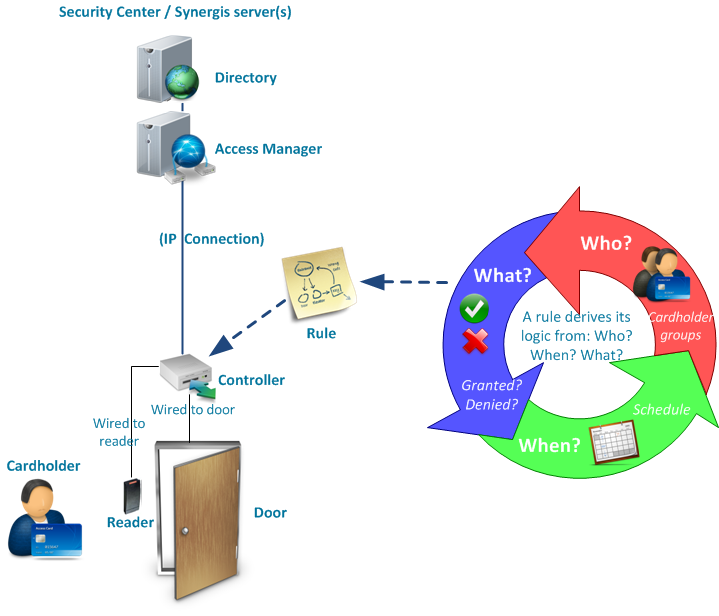
- System configurations are saved by the Directory role.
- The Directory pushes configurations to the Access Manager.
- Access Manager communicates directly with the physical door controllers, called access control units, over TCP/IP.
- Access Manager pushes schedules, cardholder information, and access rules to the door controllers.
- When a cardholder presents their credential to a reader, the controller refers to the access rule to determine whether the user should be granted or denied access.
- Once controllers have synchronized with the Access Manager, they can operate autonomously, even if they lose the network connection to the Access Manager.
With additional configuration, a cardholder can belong to a cardholder group, a door can be part of an area, and there can be multiple schedules and rules pushed to a unit.
Benefits of Synergis™
Unlike other products or solutions, Synergis™ does not use “Clearance codes” or “Access levels” to grant or deny access. Instead, the basic logic used by Synergis™ to grant or deny access is defined by the access rule.
The biggest difference between an access rule approach and an access level approach is that access rules are applied to to the access points of the physical locations we want to protect, whereas access levels are applied to people. Access rules specify who can pass through a door and when they can do so. An access level defines where and when a person can gain access.
- Who? (Who can pass through — cardholders or cardholder groups)
- What? (Whether access is granted or denied)
- When? (The schedule when the access rule is applied)
Notice that Synergis™ does not grant access to a card or credential. Rather, access is granted or denied based on the cardholders themselves. This subtle, but fundamental shift in the applied logic has a significant benefit in managing lost and stolen cards. The access rules that have been pushed to the door controllers do not have to be modified. If you associate a new credential with a cardholder, the old rule is still valid.
